Credential stuffing attacks have become more sophisticated in technology and behavior. Yet security leaders are increasingly focusing on the business dimension of it to get a fuller picture. Read this guest article from security leaders, Akamai to get deeper insights.
An account takeover (ATO), in which criminals impersonate legitimate account owners to take control of an account, causes tremendous pain for businesses in all industries. This pain may be monetary, such as losses from stolen accounts, but may also include a number of related problems, like regulatory and legal issues, lost customers, and the inability to gain new consumers due to a lack of trust. Losses from ATOs and new account fraud are estimated at more than $10 billion annually in the United States alone.
A couple of years ago, we’d usually hear about ATOs as an aspect of the attack surface that exists in the financial services industry. But now we’re seeing credential stuffing and ATOs increasing in multiple industries like media, gaming, and retail. At Akamai’s recent Edge Live Adapt event, our team talked about criminal innovations in the credential stuffing and ATO space in all of those verticals. You can view the session on demand.
ATOs are the end goal for credential stuffing attacks, where a criminal launches a bot attack to test a large number of usernames and passwords against the targeted website or service. Akamai recorded more than 100 billion credential stuffing attacks from July 2018 through June 2020.

Criminals are business people
When we think about credential stuffing, ATO, or really any other kind of automated security attack, we often worry about the sophistication of the attacker’s technology. Have they adopted new tools to better mimic human behaviors? Have they evolved their attacks to evade known detections? My colleague Tony Lauro lists many of the newer techniques used by bot operators in a recent Daily Swig article.
Firms often overlook another reason attackers are successful: their business skills. Criminal enterprises such as botnet operators work very much like legal businesses. They’ll try to pursue the best market opportunities, minimize their costs, and maximize profits. Another Akamai colleague, Jonathan Singer, recently wrote about criminal economics in the gaming industry, as an example.
Criminals even have attack workflows they follow. We call them kill chains, a term and framework developed for the cybersecurity industry by Lockheed Martin in 2011. Derived from military concepts, the kill chain is the process that criminals go through to execute on their goals. In the case of credential stuffing and ATOs, the kill chain looks like the one shown in Figure 1.
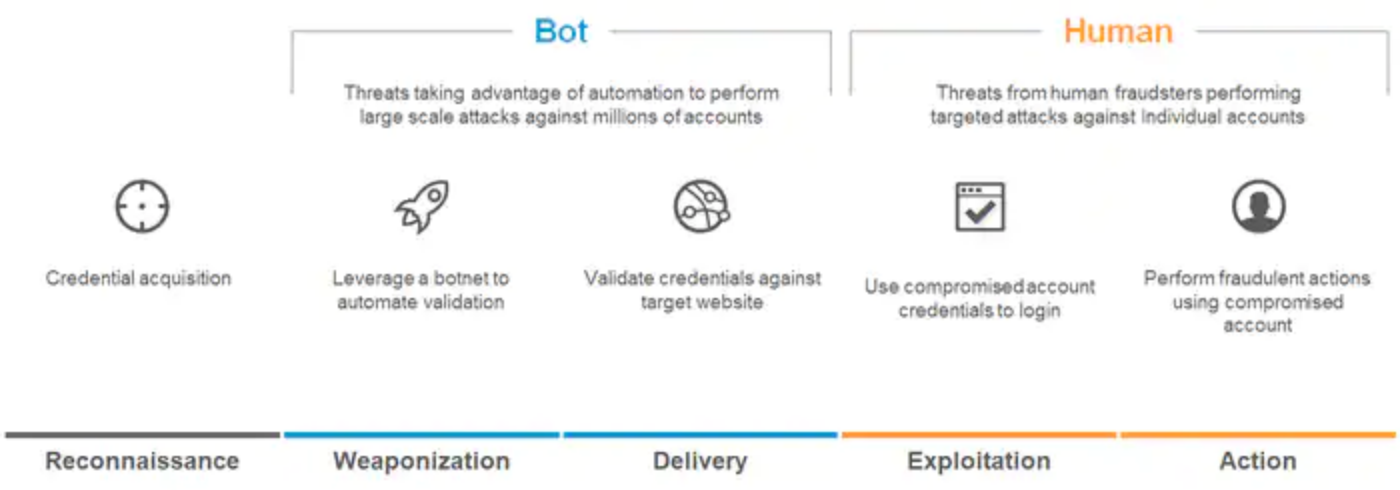
How target organizations can disrupt the kill chain
But the kill chain is the criminal’s perspective. What does the intended target organization see? And, more to the point, what can the intended target do to disrupt the kill chain? It’s an oft used trope in movies that to catch a criminal one must think like a criminal. And in the case of a credential stuffing/ATO kill chain, that means thinking like a businessperson. Rather than allow their organizations to become passive targets, security teams can put mitigations in place for each phase of the bot and human elements of the kill chain. Many mitigations focus on stopping the criminal from executing each phase, but other mitigations aim to make the attack so expensive that the attacker decides to pick an easier/less expensive target.
Diving into the concept a little deeper, we can consider a credential stuffing/ATO attack as a cat-and-mouse game, where each action taken by the attacker is met with a reaction by the intended target and vice versa. It’s a complex, co-created workflow (see Figure 2). We see that it may not be possible to completely stop an attacker in every case. But if we simultaneously focus mitigations on making it harder for the attacker to get in and making it more expensive for the attacker, we disrupt the kill chain.
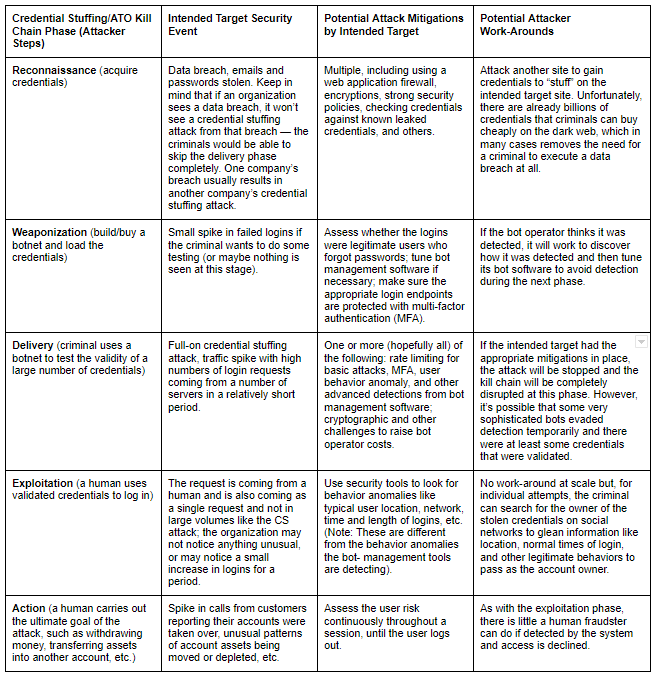
Raise attackers’ costs to lower your own
Remember that the best way to protect your business from credential stuffing and ATO is to think of the attacker as a business foe, not just a technology adversary. Raising the technical and financial costs for attackers means:
- Making attackers spend more money on hardware, compute, and human augmentation like captcha farms
- Increasing the number of stolen credentials they need to purchase in order to get credentials validated at the same rate
- Increasing the amount of time and effort needed (like phishing and social engineering) to validate credentials or to use validated ones
- Reducing the attackers’ return on investment (ROI) by lowering their probability of success and value returned relative to the cost of the attack
By increasing the technical difficulty and monetary investment of attacking your firm, you should see corollary costs go down for your organization in one or more of the following ways:
- Reduced effort and budget needed to check for compromised accounts
- For regulated businesses, mitigated risk of regulatory noncompliance, government fines, and lawsuits
- Lower costs from having to replace stolen accounts
- Minimize customer churn and tarnished brand equity
- Decreased infrastructure costs from fewer attacks and less attack traffic
- Less time demand from already-overloaded security and fraud teams
- Create business-oriented roadblocks to disrupt fraud
Attackers are always innovating their techniques and technologies as they try to execute credential stuffing and ATOs. Just like any business person, they’re striving to get better over time. To protect your customers, workers, and company, you need to innovate, too — especially in the ways you thwart attacks. Technology, implemented well, can stop many attacks, but not all of them. That’s why it’s important to also focus on the business side and find creative ways to make yourself a financially unattractive target. By taking steps to raise the attackers’ costs, make their operations less efficient, and disrupt their business model overall, you’ll better protect your business from fraud.
ABOUT AKAMAI TECHNOLOGIES
Akamai secures and delivers digital experiences for the world’s largest companies. Akamai’s intelligent edge platform surrounds everything, from the enterprise to the cloud, so customers and their businesses can be fast, smart, and secure. Top brands globally rely on Akamai to help them realize competitive advantage through agile solutions that extend the power of their multicloud architectures. Akamai keeps decisions, apps, and experiences closer to users than anyone — and attacks and threats far away. Akamai’s portfolio of edge security, web and mobile performance, enterprise access, and video delivery solutions is supported by unmatched customer service, analytics, and 24/7/365 monitoring.